Amazon S3 now offers automated Object Ownership
An interesting feature added to S3 this month may have gone unnoticed to many Simple Storage Service (S3) users, however organisations that have workloads that produce and consume data from multiple AWS accounts may enjoy this early festive season present.
Prior to this feature being available, a bucket-owner might not necessarily have control (ownership) of an object in a bucket. By default, the AWS Account that put the object in the bucket becomes the owner of the object – these permissions are governed by the Access Control List (ACL). In a cross-account environment, this object ownership and access can easily become a tricky problem to deal with, resulting in AWS account (A) not being able to read objects in a particular bucket, when the object has been put there by account (B) or bucket owner account (C).
Where you have direct control over the code that placed the object in the bucket, object ownership (the ACL) can be set, thus remediating this problem, however this is not always the case. Some commercial of the shelf (COTS) applications may not support the ACL feature, and aggregating AWS CloudTrail logs into a single account does not offer you any options to set the object ownership.
This latest S3 feature now offers you the option to essentially override the object ownership when objects are placed into the bucket. This offers you much more flexibility in terms of object access in a multi-account and cross-account data processing ecosystem and is achieved through a simple bucket policy and Condition statement:
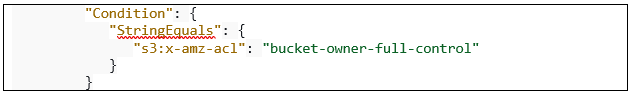
For more details on this feature and how to enable it, head to the official documentation.
Amazon CloudWatch Lambda Insights
Lambda Insights enables you to monitor, troubleshoot, and optimise the performance of AWS Lambda functions.
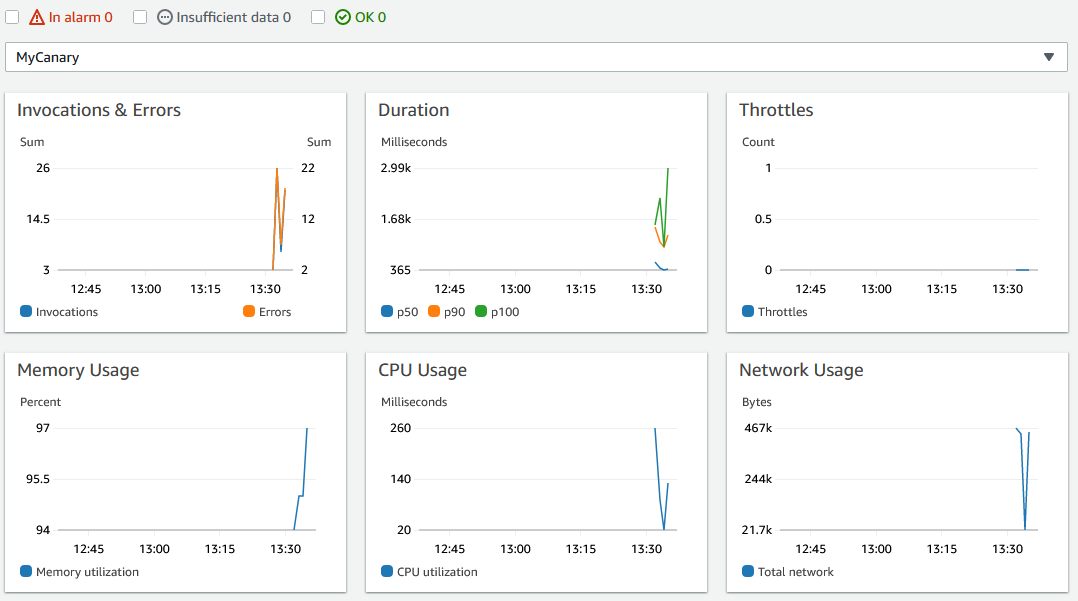
I put a very simple function together to see what Lambda Insights will offer us. As can be seen from the single-function dashboard view below, you are greeted with some “enhanced metrics” and a well-defined layout to help trace execution and performance concerns.
From the launch post:
”you can use the multi-function view to understand how compute, memory allocation, and function duration changes over time to optimize Lambda function utilization. You can use the single-function view dive deep and troubleshoot individual request problems. Additionally, to easily troubleshoot root causes of a Lambda issue you can take advantage of the integrations with AWS offerings, such as CloudWatch Logs Insights to analyze function logs and CloudWatch ServiceLens to analyze trace dependencies.”
This feature is still in preview and best of all you do not have to apply to access the preview (noting of course that this means aspects of it may change prior to it being officially made generally available).
For more information on CloudWatch Lambda Insights, refer to the documentation here.
